Digital Certificates
16 March 2025
Digital Certificates are one of the foundation blocks of security in digital world. They are used to authenticate the identity of the device and secure the transactions between devices. Digital certificate is a data structure that contains various parameters that can be used to establish trust. This section provides an overview of the digital certificates.
Let us dive into few concepts:
Symmetric key cryptography
In Symmetric key cryptography same key is used to encrypt and decrypt.
- Advantage: They are faster to encrypt and decrypt
- Disadvantage: The secret key has to be shared between the sender and receiver.
Secure key distribution is a major problem to be solved, and this is where the Asymmetric key cryptography excells
Asymmetric key cryptography (public key cryptography)
Asymmetric key cryptography solves the above mentioned key distribution problem by using 2 keys (key pair) instead of a single shared key.
- One of the keys is kept secret - private key
- Other key is made public - public key
There are different algorithm choices available for asymmetric key cryptography. Some of the popular ones are:
-
RSA - Rivest–Shamir–Adleman.
- Most suited for communication encryption
- Based on difficulty of Prime factorization
-
DSA - Digital Signature Algorithm
- Most suited for signing (encrypting hash) and verification
- Based on difficulty of discrete logarithm
-
ECC- Elliptic Curve Cryptography
- Greater cryptographic strengh for equivalent key size in RSA/DSA
Some algorithms like RSA technically allows YOU to choose which key is private and which is public. But some others like ECC does not give you a choice as they are dissimilar in computation.
Hybrid approach
The Asymetric encryption is computationally heavy (could be 1000s of times heavy) as compared to the symmetric encryption. In practical usecases a hybrid approach is used where public key cryptography is used for securely sharing symmetric key. After this initial step, the symmetric key is used always.
Majority of the communication encryption usecases follows a hybrid approch.
Assymetric encryption - Key aspects
Sharing
- Public keys can be shared to anyone publicly. There is no secrecy involved here.
- Private keys are not shared with anyone else.
Public keys can be shared via different mechanisms . For example:
- Manually via email or similar mechanisms
- Using a protocol, like TLS
Oneway Encryption
- If public key is used to encrypt the message, only the private key can be used to decrypt the message.
- If private key is used to encrypt the message, only the public key can be used to decrypt the message.
Alice shares public key to rest of the world including Bob. Bob uses it to encrypt data and send to Alice. Alice decrypts with private key. Nobody else can decrypt it since they don't have private key
Jac plays the trick
Jac can access Alice's public key since it is shared to the world. Jac uses Alice's public key and sends Alice a message impersonating Bob "Hello, I am Bob !". Alice will be able to decrypt it with her private key. Alice thinks it came from Bob, and may respond to him!
To avoid this, digital signatures are used. Bob signs the message using Bobs private key. Alice always uses Bobs shared public key to verify the signature. Now Jac cannot impersonate Bob since Jac don't have Bobs private key to sign the message.
A protocol like TLS includes the full mechanism to handle all these aspects using digital signatures. To know more about TLS, visit: below article:
ssl library performs the verification of certificate date, CA signature verification by default. This is part of TLS handshake protocol specficcation.
A check is required to ensure that the domain mentioned in the certificate and the domain is used in the connection is matching. This check is not part of TLS protocol, but it is avalable as part of the ssl libraries. During the TLS connection establishment time, ssl library is given in the input parameter of the domain or IP to validate against. When the digital certificate is downloaded as part of the TLS handshake, ssl library checks the download IP and IP mentioned in the certificate is matching. Certificate validation will be failiing if not matching. This is an optional feature of the ssl library.
Similarly a certificate revocation checks are also done in ssl library, but it is not part of the TLS protocol.
What is a digital certificate ?
A digital certificate is a file that contains following compoenents:
- Public Key
- Digital signature of the certificate hash
- Asymmetric encryption algorithm used
- Hashing and Signature Algorithm used, like sha256RSA
- Certificate version
- Issuer - Name of the CA that issued and signed the certificate
- Subject - Subject to which this certificate is assigned
- And more ...
Digital certificate standard
X509 is a standard for publick key digital certificate. All X509 objects are represented in Abstract Syntax Notation One as a byte array.
Digital certificate file encoding formats
Below are the popular certificate file formats:
- PEM - X509 in ASCII format (Base64 encoded)
- DER - X509 in binary format (ASN1 encoded in binary)
- PKCS12 - A password-protected container format that contains both public and private certificate pairs. It is fully encrypted. This can contain private key and certificate chain material. This is a Microsoft standard.
- PKCS7 - Does not contain private key material. This is a Java open standard
- CER - Windows certificate file name in PEM or DER format. Only extension is changed
- CRT - Unix certificate file name in PEM or DER format. Only extension is changed
- And more ...
Signature Algorithms
In a digital certificate (like an X.509 certificate), the portion that gets signed is called the "TBSCertificate"(To Be Signed Certificate). After signing The result is stored in the signatureValue field of the certificate"
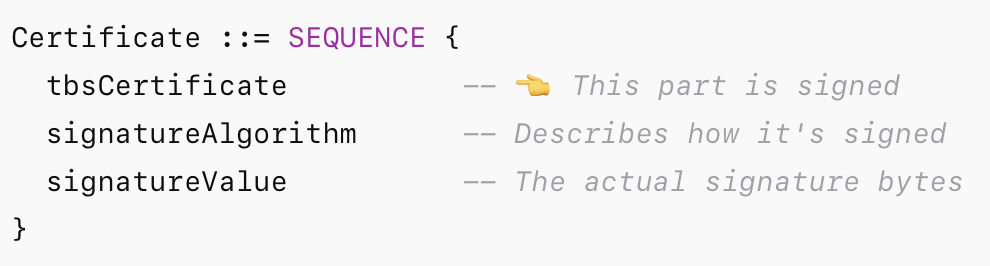
Signing process
- Hash the data using algorithms like SHA-1
- Encrypt the digest with the sender's private RSA key
- The result stored in signatureValue field of the certificate
Various algorithms can be used for signing it. Examples below:
-
RSA-Based Signature Algorithms
- sha1WithRSAEncryption - Deprecated
- sha256WithRSAEncryption - Secure
- sha384WithRSAEncryption - Stronger
- sha512WithRSAEncryption - Strongest
-
ECDSA-Based Signature Algorithms
- ecdsa-with-SHA1 - Deprecated
- ecdsa-with-SHA256 - Common
- ecdsa-with-SHA384 - Stronger
- ecdsa-with-SHA512 - Strongest
-
EdDSA-Based Signature Algorithms
- Ed25519 - Fast, strong, and modern
- Ed448 - Even stronger but less commonly supported
-
RSA-PSS (Probabilistic Signature Scheme)
- RSASSA-PSS - More secure than PKCS#1 v1.5 RSA
-
Deprecated / Legacy Algorithms (Avoid)
- md5WithRSAEncryption - MD5 is broken
- sha1WithRSAEncryption - SHA-1 is broken
- ecdsa-with-SHA1 - SHA-1 is broken
Fingerprint Algorithms
- A signature is created by the issuer using their private key, and it's used to validate the authenticity of the certificate
- A fingerprint is a hash value of the certificate's entire DER-encoded content (binary format).
- A fingerprint is just a hash — no signing involved. It's used more for identification and comparison than validation
- If any part of the certificate is modified (even one bit), the fingerprint will change. You can manually verify the fingerprint against a known trusted value — for example, if your organization publishes the correct fingerprint for internal servers
-
Typical fingerprint algorithms used
- SHA-1 (legacy)
- SHA-256 (modern, recommended)
- MD5 (deprecated, insecure)
-
Usecases
-
Certificate Trust Verification
- Manually verifying a certificate from a source (website, app, server) - “Here’s the SHA-256 fingerprint of our SSL certificate. Make sure it matches.”. Example: SSH key verification or installing a root CA cert
- You compare the fingerprint shown locally to the one published on a trusted website or document. If they match, you can trust it. If they don’t tampering might’ve occurred
-
SSH Host Key Verification
- "Is this the real server, or is someone pretending to be it?" - The first time you connect, you have to trust the fingerprint or compare it with a known-good value
- When you ssh for first time, you may see a message "The authenticity of host 'example.com' can't be established. RSA key fingerprint is SHA256:abcd1234...Are you sure you want to continue? "
- This is a fingerprint of the server’s SSH key.
- At this point, you're supposed to compare this fingerprint to a value provided by your sysadmin
-
Working
- SSH client receives the server's public key
- SSH client It hashes that key using a fingerprint algorithm
- It compares that hash against any known fingerprints in your ~/.ssh/known_hosts file
- If it matches, you're good
- If it doesn't, you get a warning (maybe a MITM attack, or maybe the server reinstalled).
-
Certificate Pinning
- Mobile apps and web apps can “pin” a fingerprint (SHA-256 of the cert) instead of trusting just a CA
- Even if a valid cert is issued by a trusted CA, if it doesn't match the pinned fingerprint, the app refuses to connect
- Used by banks, messengers, and secure apps
- In ssh, you can manually pin a known fingerprint to a host using the known_hosts file . This prevents SSH from silently accepting unknown keys
-
Identifying and Organizing Certificates
- In enterprise environments with hundreds or thousands of certs, fingerprints help you track and identify specific certificates
- Tools like browsers, certificate managers, and cloud dashboards often show fingerprints for visual verification
-
Certificate Trust Verification
Self signed digital certificates
A self-signed certificate is a digital certificate that is signed by the entity it is issued to, rather than a trusted Certificate Authority (CA).
In a self signed certificate:
- The issuer and subject are the same
- It’s signed with its own private key, not by a certificate authority (CA).
You’ll usually also get a big "Not Trusted" warning unless you’ve added it to your trusted store
Types of digital certificates
Although underlying technology is the same, there are different types of digital certificates depending on the usecases. Digital certificates can be categorized based on differences in X.509 fields.
-
By Validation Level (based on Subject fields and CA checks)
- These differ mainly in the Subject field and what the CA verifies before issuing
-
Domain Validation (DV) Certificates. Domain ownership only.Basic website encryption.
- Validates: Only the domain ownership
- Subject Fields: Minimal — typically just CN or SAN with the domain name
- Usage: Basic HTTPS for websites
- SAN field must match the domain
- Subject fields like Organization (O), Location (L), etc. are often blank or not validated
-
Organization Validation (OV) Certificates
- Validates: Domain ownership and the organization's identity
- Subject Fields: CN, O (Organization), C (Country), L (City), ST (State).
- Usage: Business websites, APIs, internal tools
- Includes full Subject DN fields with verified organizational info
- May include organization info in certificate extensions
-
Extended Validation (EV) Certificates
- Validates: Domain ownership and a rigorous check of the organization's legal identity
- Subject Fields: Same as OV but with stricter verification
- Usage: High-trust websites (banks, e-commerce, etc.).
- Same fields as OV, but often includes special OID in extensions (e.g., EV policy OIDs)
- Recognized by browsers with visible indicators (green bar in older browsers, etc.).
-
By Usage (based on Key Usage & Extended Key Usage extensions)
- These differ in keyUsage and extendedKeyUsage fields
-
SSL/TLS Certificates
- Purpose: Secure websites (HTTPS).
- Key Usage: Digital Signature, Key Encipherment
- Extended Key Usage: TLS Web Server Authentication, TLS Web Client Authentication
-
Email Certificates (S/MIME)
- Purpose: Secure email communications
- Key Usage: Digital Signature, Key Encipherment
- Extended Key Usage: Email Protection
- Subject Fields: Often includes an email address
-
Code Signing Certificates
- Purpose: Verify software/app authenticity
- Key Usage: Digital Signature
- Extended Key Usage: Code Signing
- Subject Fields: Organization name is typically included
-
Client Authentication Certificates
- Purpose: Authenticate users/systems
- Extended Key Usage: Client Authentication
-
Document Signing Certificates
- Purpose: Sign PDFs, Word docs, etc
- Extended Key Usage: Document Signing
-
By Trust Model (based on issuer fields)
-
Root Certificates
- Self-signed
- Used to sign intermediate CAs
- Issuer = Subject
-
Intermediate Certificates
- Issued by a root or another intermediate CA
- Used to issue end-entity certs (like DV/OV/EV certs).
- Helps with trust chain hierarchy
-
End-Entity Certificates
- Issued to servers, users, or devices
- Used in actual authentication/communication
- Cannot sign other certificates (CA:FALSE in Basic Constraints). Need for this: If a certificate without CA:FALSE is compromised and it can issue other certificates, an attacker could create fake certs for any domain — a massive security risk.Root & Intermediate CAs: CA:TRUE and Leaf (end-entity) certs: CA:FALSE
-
Root Certificates
Non X.509 digital certificates
-
PGP Certificates (Pretty Good Privacy)
- Format: OpenPGP
- Not based on X.509 at all
- Used in email encryption, file signing, and tools like GnuPG (GPG)
- No central certificate authority (CA); uses a "web of trust" model instead of PKI.
- Certificates contain: User ID (name, email), Public key, Signatures from other users (for trust)
- Decentralized trust, user-to-user verification
-
SSH Public Keys
- Not certificates in the X.509 sense, but they’re used to authenticate users/hosts
- SSH keys are raw key pairs (e.g., RSA, Ed25519), often stored in: ~/.ssh/id_rsa.pub, /etc/ssh/ssh_host_rsa_key.pub
- Can optionally be wrapped in OpenSSH certificate format
- These certificates are not X.509, but serve a similar purpose (signed public keys with metadata)
- Lightweight, flexible, and mostly used in internal or dev environments
-
S/MIME Certificates (Older Versions)
- Modern S/MIME uses X.509, but some older or proprietary formats used custom certificate structures. Some early email systems or vendors had their own crypto formats before standards unified around X.509
-
JSON Web Tokens (JWTs) with Public Keys
- Not exactly certificates, but serve similar purposes in identity and authorization
- A JWT can include a JWK (JSON Web Key), which can be verified using a public key
- Common in OAuth 2.0, OpenID Connect, and API token systems
- Web-native, token-based identity, often with signed payloads
PGP Certificates
PGP is based on decentralized trust - There’s no central authority that everyone must trust to verify identities. Instead, you decide who you trust, and you can trust other people's trust. This is in contrast with CA-based (centralized trust).
In centralized trust YOU don’t decide who to trust — your software or OS does. In PGP, you build your own trust relationships
- In PGP each person generates their own key pair (no CA needed)
- Each person shares their public key with others (often on keyservers)
- Each person can sign someone else's key to vouch for it
- If you trust Alice, and Alice signs Bob’s key → you might trust Bob, too. This forms a web of signatures and trust links
- This is why it's called a Web of Trust — decentralized, organic, and based on human trust relationships
Fields in digital certificates X.509
X.509 digital certificates, commonly used in SSL/TLS for secure communication, have a standardized structure defined by the X.509 specification
-
Basic Certificate Fields
- Version - Indicates the X.509 version (v1, v2, v3).
- Serial Number - A unique identifier assigned by the issuing Certificate Authority (CA)
- Signature Algorithm - Specifies the algorithm used by the CA to sign the certificate
- Issuer - The entity that issued the certificate (usually a CA). Includes details like Common Name (CN), Organization (O), Country (C), etc
- Validity Period - Not Before: The start date/time the certificate is valid, Not After: The expiry date/time
- Subject - The entity the certificate is issued to. Includes fields like Common Name (CN), Organization, Country, etc
- Subject Public Key Info - Algorithm: The public key algorithm (e.g., RSA, ECDSA), Public Key: The actual public key
-
Extensions (v3 certificates only)
- Basic Constraints - Indicates if the certificate is a CA certificate or not. Example: CA:TRUE or CA:FALSE
- Key Usage - Specifies the intended usage of the public key . Examples: Digital Signature, Key Encipherment, Certificate Signing
- Extended Key Usage - More specific usage purposes. Examples: TLS Web Server Authentication, Code Signing
- Subject Alternative Name (SAN) - Lists additional identities like DNS names or IP addresses. Crucial for modern HTTPS (often more important than CN).
- CRL Distribution Points - URL(s) where the Certificate Revocation List can be obtained
- Authority Key Identifier - Identifies the public key of the CA that issued the certificate
- Subject Key Identifier - A unique identifier for the certificate’s public key
- Authority Information Access - Provides methods to access the issuing CA’s certificate or Online Certificate Status Protocol (OCSP) responder
Importance of Subject Alternative Name (SAN)
- The Subject Alternative Name (SAN) is one of the most important extensions in modern X.509 certificates, especially for web security and HTTPS
-
SAN replaces the legacy Common Name (CN) for domain validation
- Historically, the Common Name (CN) field in the Subject was used to specify the hostname
- Modern browsers and clients now rely on SAN instead of CN to validate the domain
- If SAN is missing, many clients (especially modern browsers like Chrome, Firefox) will reject the certificate, even if the CN is correct
-
Supports multiple domain names
-
SAN allows a single certificate to secure multiple domains or subdomains, like:
- example.com, www.example.com, mail.example.com, api.anotherdomain.com
- This is particularly useful for: Multi-domain SSL certificates, Wildcard-like support (to some extent, though not identical)
-
SAN allows a single certificate to secure multiple domains or subdomains, like:
Wildcard digital certificates
A wildcard certificate is a type of SSL/TLS certificate that secures a domain and all of its subdomains at a single level using a wildcard character (*).
Certificate for *.example.com covers: www.example.com, mail.example.comm blog.example.com etc. But it does not cover: sub.mail.example.com (that’s a second-level subdomain) or example.org (different root domain)
Usecases
- Hosting multiple subdomains on a single certificate. Example: A web hosting company with clients on client1.hosting.com, client2.hosting.com, etc. Saves cost and effort compared to managing separate certs
- Dynamic subdomain creation. Great for SaaS platforms where each customer gets a subdomain (e.g., user1.app.com, user2.app.com).
- Simplifies certificate management - Fewer certificates to track and renew. Ideal for organizations with large internal infrastructure or microservices architecture
- Cons - Security risk: If one private key is compromised, all subdomains are vulnerable
- Cons - Doesn't cover deeper levels: *.example.com ≠ a.b.example.com
- Cons - Some Certificate Authorities limit wildcard support (e.g., not allowed for EV certs)
SHA-1 digital certificate
-
A SHA-1 digital certificate is an X.509 certificate (used in HTTPS, email security, code signing, etc.) that
uses the SHA-1 (Secure Hash Algorithm 1) cryptographic hash function in one or more of the following areas:
- Signature Algorithm – The certificate is digitally signed by a Certificate Authority (CA) using SHA-1, often shown as something like sha1WithRSAEncryption.
- Thumbprint / Fingerprint – SHA-1 is used to generate a fingerprint of the certificate (not related to trust, just an identifier).
-
SHA-1 certificate is deprecated as it is considered cryptographically broken. Most browsers, operating
systems, and CAs now reject or warn against SHA-1 certificates
- Signature Algorithm: sha1WithRSAEncryption - is not ok
- Fingerprint Algorithm: SHA-1 Fingerprint - is ok. still common for identification, not used for security
- SHA-256 or better (SHA-2 family) is now the standard
SHA-2 digital certificate
- Most Common Today.
- SHA-2 family of hash functions includes - SHA-224, SHA-256 (most widely used), SHA-384, SHA-512
Working of PKI
- You will generate a key-pair
- You will keep the private key secret
-
Certificate Signing Request (CSR) is made for a domain name or multiple domain names. CSR includes your public
key information and information about your domain inside a configuration file. CSR is then sent to CA. Below
command generate key pair having password protected private key, and a CSR.
$ openssl req -newkey rsa:2048 -keyout crispinjacob.com.key -out crispinjacob.com.csr
- CA verifies crispinjacob.com.csr and signs your public key and related information in the form of a signed public key certificate
- You will install your signed certificate in your server
- You will install your private key in your server. This private key is password protected while generating it. Only your server can use this private key.
- A webbrowwer or client application access your server and TLS handshake occures, and publick key certificate is downloaded to browser as part of HTTPS handshake
- Browser verifies the received server certificate before trusting it - validiyt, connected domain and domain name the certificate and so on.
- The certificate verification is baed on a trust achor that browser has access to. Trust anchor is a CA certificate that is often distribuited along with browser, or store in the OS that the browser trusts. Browser expects the downloaded server certificate is signed by this CA certificate (trust anchor)
-
In most cases the server certificate is not signed by the root CA that comes with OS or brower. That will be
another CA that the trust anchor CA trusts . This is called an intermediate CA.
In this case, the brower checks who signed the intermediate certificate. If it is signed by one of the trust Anchors then the brower trusts the downloaded server certificate. This verification is performed by decrypting that intermediate CA signature using trust anchors (root CA) public key. -
Often a further lower hierarchy CA might have signed the server certificate.
in this case, the brower verifies the issuer CA signed the server certificate, by decrypting server certificate signature with issuer CA public key. Then browser verifies the parent CA that signed the CA. This process goes from leaf node server certificate, up till trust anchror which is often the trust anchor certificate. If successful, at that point , the trust is established on the serer certificate.
Note that if you install one of the intermediate CA certificate in your brower/OS, then that will be your trust anchor, and you dont need to check till root CA. Often the entire chain of certificate is downloaded in single shot during TLS handshake. Note that if your browser misses one of the intermediate certificates, then your certificate's verification will fail.
Trust anchor
A trust anchor is the root certificate (or public key) that your system or application explicitly trusts. It’s the starting point for validating a chain of trust. If a certificate chain ends in a certificate that matches one of your trust anchors, the whole chain is considered trustworthy (as long as everything else checks out, like signatures and validity periods).
An intermediate certificate can be a trust anchor, if you explicitly configure it as one. A trust anchor is stored in the system/browser/application’s trusted root CA store. But technically any certificate (including an intermediate) can be made a trust anchor if you configure it that way. When you do that, validation stops at that certificate, and no parent (like a root) is required. Let’s say you’re in a private network or using enterprise PKI, and you don’t want to trust a public root CA. Then you might trust a private intermediate CA as your trust anchor. This is valid — and often used in custom or constrained environments
When a certificate is configured as a trust anchor, it's not validated like the rest of the chain. You’re telling the system: “I trust this cert — no questions asked.”
Certificate Chain
Server the entire certificate chain (except for the root certificate) is typically sent by the server during a TLS handshake. Certificate chain is based on chain of trust concept.
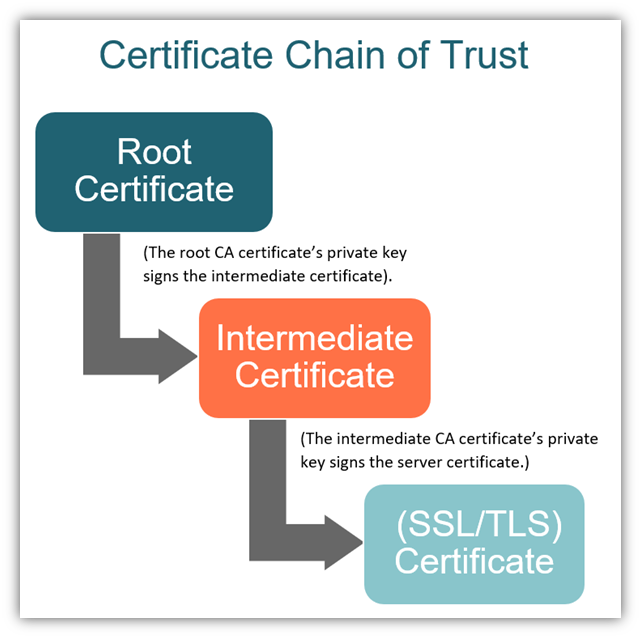
The certificate chain usually includes:
- Server certificate (e.g., www.example.com) – proves the identity of the server
- Intermediate certificate(s) – one or more certs that link the server cert to a trusted root
- Root certificate – usually not sent by the server, because It's already known and stored in the client's trusted root CA store (like in browsers or OS). It's assumed that clients already have a set of trusted root certificates installed. Sending it would just waste bandwidth
When you view the certificate chain in a browser, sometimes you'll see the root certificate included in the chain. The browser didn’t get that root cert from the server during the TLS handshake. It pulled it from the local trust store and shows it in the chain for completeness. Browser is trying to display the full trust path, from the server cert all the way up to a trusted root. Even though the server didn’t send the root cert, the browser knows it's trusted (because it’s in the OS/browser trust store), so it includes it in the UI
The sender decides the certificates includes in the certificate chain. For example sender may exclude unnecessary certificates, like trusted root certificate. It's considered a best practice to configure your webserver to deliver the full chain.
If the certificate chain size exceeds TCP’s initial congestion window, it caan cause roundtrips to the TLS handshake. As newer TCP stack has initial congestion window increased to 10 TCP segments this is sufficient for most certificate chains.
Certificate validation
Many libraries (like OpenSSL, BoringSSL, Java's PKIXValidator, .NET, etc.) implement certificate validation according to RFC 5280, though behavior can slightly vary in edge cases (e.g., revocation policy, fallback logic).
RFC 5280 is the gold standard for certificate validation rules in most of the internet. Key steps for certificate validation as defined in RFC
- Build a valid chain from the end-entity cert to a trusted anchor
- Verify each signature in the chain
- Check validity periods (notBefore / notAfter)
- Respect path length constraints (e.g., how many intermediates are allowed)
- Honor extensions (like whether a cert is allowed to sign other certs)
- Check for revocation (via CRLs or OCSP)
- Enforce name constraints and policies, if present
In most real-world cases client validates the certificate chain during the TLS handshake
Client should always validate the certificate, but it may not do that in some cases.
- Manually disabled validation (dangerous in production! Exposes you to MITM attacks) - Testing/local development, Self-signed certs without adding them to the trust store, Speed/complexity reasons (common in quick-and-dirty scripts)
- Custom validation logic - Some apps override the default logic. Accepting only certs signed by a specific intermediate, Performing extra checks (e.g., matching Common Name or SAN), Skipping revocation checks for speed
- Non-TLS protocols or legacy systems - Some old or proprietary protocols might use TLS but skip validation due to poor implementation
Domain name verification is a critical part of certificate validation, especially for TLS/HTTPS. When a client connects to a server using HTTPS (like https://example.com), it must check that the server’s certificate is issued to that exact domain. This is called Hostname (or domain name) verification
The client compares the requested domain name against: The Subject Alternative Name (SAN) field in the certificate, (Legacy fallback) The Common Name (CN) field in the Subject. This is defined in RFC 6125, and reinforced by TLS specs. Example: You go to https://mail.google.com . The server sends a cert with SANs like: DNS:*.google.com, this is valid. But if the cert only says DNS:api.example.com, then it is invalid for mail.google.com
Verifying the domain name (hostname) is an essential part of certificate validation in HTTPS and other secure protocols. This validation is not part of the TLS protocol, but required by applications using TLS (like HTTPS, SMTP, etc.). TLS does not define how to match the certificate to the hostname. That’s left up to the application layer protocol.
TLS itself implement certificate validation via the TLS libraries. not directly in the TLS protocol spec. The TLS protocol (e.g., TLS 1.2, TLS 1.3) defines that certificates are exchanged and must be validated. But it doesn't say how to do that validation in full detail. Instead TLS libraries (like OpenSSL, BoringSSL, GnuTLS, SChannel, etc.) are responsible for implementing Certificate parsing, Chain building, Signature verification, Extension checks (e.g., key usage, constraints), Revocation checking (optional). These libraries typically follow RFC 5280 for validation logic
Revoking a certificate
One method is to periodically download Certificate Revocation List (CRL) and inspect every certificate in the list. If the certificate is in revocation list , the certificate verification will be made to fail. This is not a scalable nechanism.
The alternate mechanism is to use a protocol Online Certificate Status Protocol (OCSP).OCSP helps the client to check the validity of the certificate using a query instead of storing a list. The CA also need to support OCSP protocol.
In OCSP Stapling protocol, the server retrieves OCSP response and sends to client during the handshake. As OCSP resonse is signed by CA, the client can verify it
How OCSP Works:
- Client receives a server certificate (during TLS handshake)
- Client extracts the OCSP responder URL from the certificate's Authority Information Access (AIA) extension. Example "OCSP - URI:http://ocsp.digicert.com"
- Client sends a signed OCSP request to that OCSP responder
- OCSP responder (run by CA) replies with one of good, revoked, unknown
- If revoked, connection is usually terminated
- If good, client proceeds with the connection
Optimisation:
- OCSP is a real-time protocol to check if a certificate has been revoked
- Normally, every client hits the OCSP server → slower, privacy risk, DoS vector
- OCSP Stapling to the rescue - The server fetches and caches its OCSP response
- During TLS handshake, the server "staples" the OCSP response to the certificate
- The client doesn’t have to contact the OCSP responder → faster and private. This is what modern HTTPS servers (like NGINX, Apache, etc.) should use
Working of CRL:
- OCSP and CRL both exist to solve the same problem of detecting whether a certificate has been revoked (as compared to sending the cert’s serial number to the CA’s OCSP server)
- Client downloads a full list of revoked certificates from the CA
- Then checks: “Is the cert I’m verifying in this list?”
- CRL: Can grow into hundreds of KB or more as the CA revokes more certs over time
- Both CRLs and OCSP responses must be Digitally signed by the issuing CA
SAN (Subject Alternative Name) and CN (Common Name)
The difference between SAN (Subject Alternative Name) and CN (Common Name) is a big deal in modern TLS/PKI. SAN is the modern, preferred way to specify valid hostnames. SAN supports multiple domains in one cert (multi-SAN or multi-domain certs). Modern browsers and TLS clients check SAN only. No SAN = invalid cert in most systems today (even if CN matches)
Common Name (CN) is legacy way to specify the hostname. It was, originally used to identify the cert's primary domain. CN is deprecated (but still supported for compatibility)
CA:FALSE constraint in certificates
It means this certificate is not allowed to act as a Certificate Authority (CA). So it cannot issue other certificates — it's an end-entity certificate (also called a leaf certificate).
- CA certs → CA:TRUE - Can sign and issue other certificates
- End-entity certs (like websites) → CA:FALSE - Cannot sign or issue certs — they're at the bottom of the chain
Assume an attacker gets access to an end-entity cert’s private key, the cert does not have CA:FALSE and validation client is misconfigured or vulnerable. The attacker can then use the stolen private key to Generate new bogus certificates for domains they don’t own like login.microsoft.com, and sign them using the compromised cert as the "issuer". Without CA:FALSE, the only thing preventing a cert from being a CA is... 'Hope'
CA:FALSE is a critical defense-in-depth control.
When validating a certificate chain, the TLS or PKI software will Reject any certificate in the chain (except the last one) that has CA:FALSE because intermediates must be CAs. Accept CA:FALSE only on the leaf
. Think of it like marking a key "For Office Use Only" — it's not just about security, it’s about intent enforcement
CA creating a fake certificate and fake webserver
Often the rootCAs are and trusted. But when it comes to intermediates CAs of small size, there is a possibility of malicios actors. If your intermedicate CA issues a fake certificate using your domain name, you wont come to know about it. This certificate can be used for man in the middle attack since the brower will trust your domain name
Common certificate errors in browser
The reasons for errors (e.g., expired cert, bad hostname, untrusted CA) are defined and consistent across the industry, But the error messages are not standardized across browsers. Don't expect the same code or label, even if the underlying issue is identical
-
Your connection is not private/ ERR_CERT_COMMON_NAME_INVALID
- The domain name in the certificate doesn’t match the one in the browser’s address bar
- Cert is for www.example.com, but you're visiting example.com
- Cert has no SAN extension (legacy issue)
- You’re using an IP address instead of the domain
-
Certificate not trusted/ERR_CERT_AUTHORITY_INVALID
- The certificate was not issued by a trusted CA
- The browser doesn’t trust the chain
- Self-signed certificate (e.g., dev environments)
- Intermediate cert missing from server chain
- Cert issued by a private CA (without installing the CA cert locally)
- Expired or revoked root/intermediate
-
Certificate expired/SEC_ERROR_EXPIRED_CERTIFICATE
- The certificate’s validity period has passed
- Renew the cert
-
Incomplete certificate chain/ERR_CERT_AUTHORITY_INVALID
- The server isn’t sending the full chain (missing intermediate CA certs).
-
Certificate revoked/SEC_ERROR_REVOKED_CERTIFICATE
- The certificate has been revoked by the CA (e.g., due to compromise).
-
Invalid certificate usage
- Certificate is being used for the wrong purpose. Example: using a code-signing cert for HTTPS
- Fix: Issue or install the correct type of cert (TLS/SSL cert for web)
-
Self-signed certificate
- Certificate is signed by itself, not a trusted CA
- Common in dev/test environments
-
Weak signature algorithm/ERR_CERT_WEAK_SIGNATURE_ALGORITHM
- Certificate uses SHA-1, which is deprecated due to security flaws
-
SEC_ERROR_BAD_SIGNATURE
- The certificate’s signature doesn't match the data - Possibly a tampered cert
Private key storage
-
Store in file system
- File permissions: only readable by the service
- Password encryption: often encrypted with a passphrase
- .key file format. A .key file is a file that stores a private key — usually in PEM (Privacy Enhanced Mail) format. It's just the private key (not the certificate).
-
Operating System Key Stores
- Windows Certificate Store - Stores private keys in the user or machine scope, Apps like IIS, Chrome, Outlook access it, Keys can be marked as non-exportable
- macOS Keychain - Used by Safari, Mail, etc
- Linux/Unix - GnuPG/Seahorse for PGP, NSS database (used by Firefox), OpenSSL often uses .pem or .key files
-
Hardware Security Modules (HSMs)
- Purpose-built hardware devices for key storage - Keys never leave the device, Used in high-security environments (banks, cloud providers, gov), Can generate, sign, decrypt — without exposing the key. AWS CloudHSM, Azure Key Vault with HSM-backed keys, YubiHSM, SafeNet HSMs
-
Trusted Platform Module (TPM)
- Built into many laptops/servers - Hardware chip for key storage, Used by BitLocker (Windows), Secure Boot, etc, Keys are bound to the physical device
-
Smart Cards & USB Tokens
- Store keys on a physical token, Often require a PIN to , Used in high-assurance identity systems. YubiKey, CAC cards (used by U.S. DoD), PIV-compliant tokens
-
Cloud Key Management Services (KMS)
- Managed key storage, signing, and encryption APIs, AWS KMS, Azure Key Vault, Google Cloud KMS, You don't directly access the private key, You call the service to sign/decrypt, and the key never leaves